As this blog and others have discussed, exploit kits are frequently used to deliver malware payloads onto victim systems. Clicking a malicious link in a phishing email, visiting a compromised site, or malvertising on a legitimate site are among the techniques most commonly used by threat actors to lead victims to exploit kit (EK) servers.
In late August, Proofpoint detected an infection attempt via malvertising that showed just how popular these services can be with threat actors. The initial redirector pulled in the Angler exploit kit; unsurprisingly since Angler currently accounts for approximately half of total EK activity, according to Proofpoint statistics [1]. (Fig. 1)
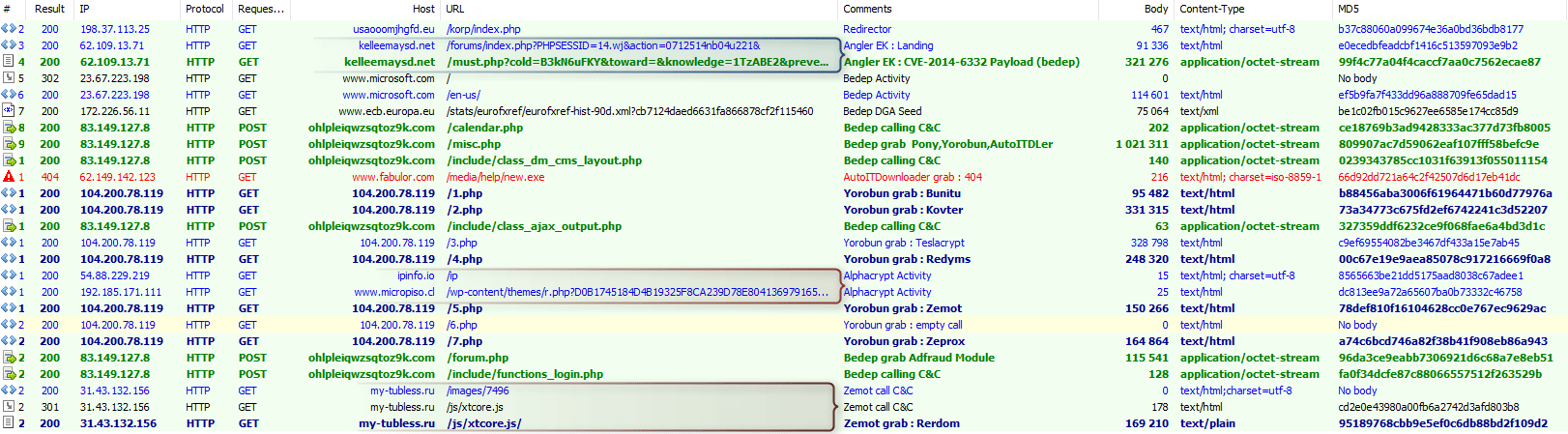
Figure 1: Initial redirect and landing on Angler EK
However, after Angler opens the door things get interesting, as a subsequent traffic capture shows. (Fig. 2)
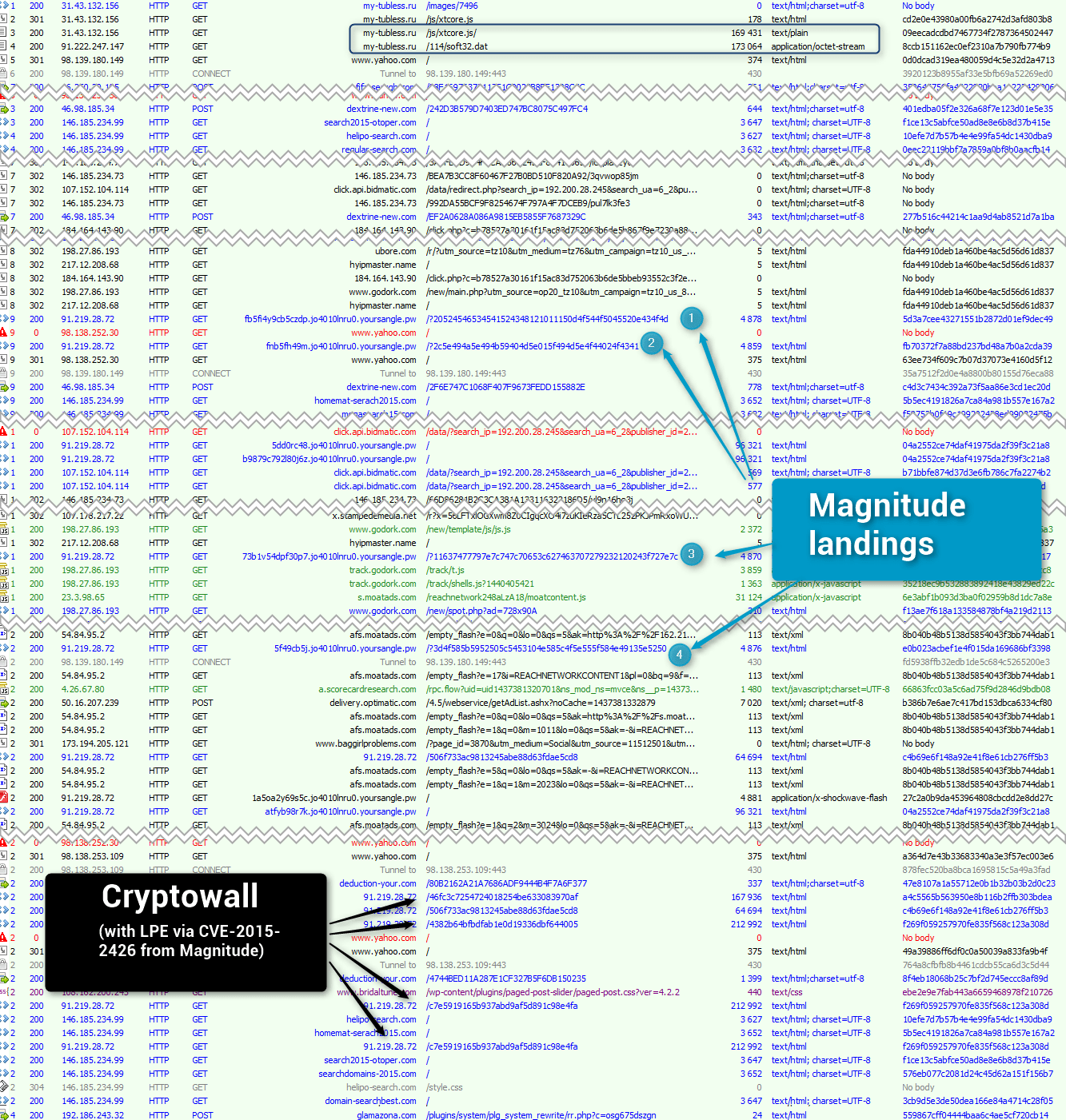
Figure 2: Traffic capture of Magnitude portion of infection chain
This traffic capture shows that Zemot [2] payload pulls in Magnitude via two redirectors:
Onlinehyips[.]net
Hyipmaster[.]name
And uses the following referers :
[hxxp://regular-search[.]com/]
[hxxp://search2015-otoper[.]com/]
[hxxp://homemat-serach2015[.]com/]
[hxxp://domain-searchbest[.]com/]
The end result is an infection chain that resembles a malware clown car, as one payload after another attempt to pile onto the targeted client. (Fig. 3)
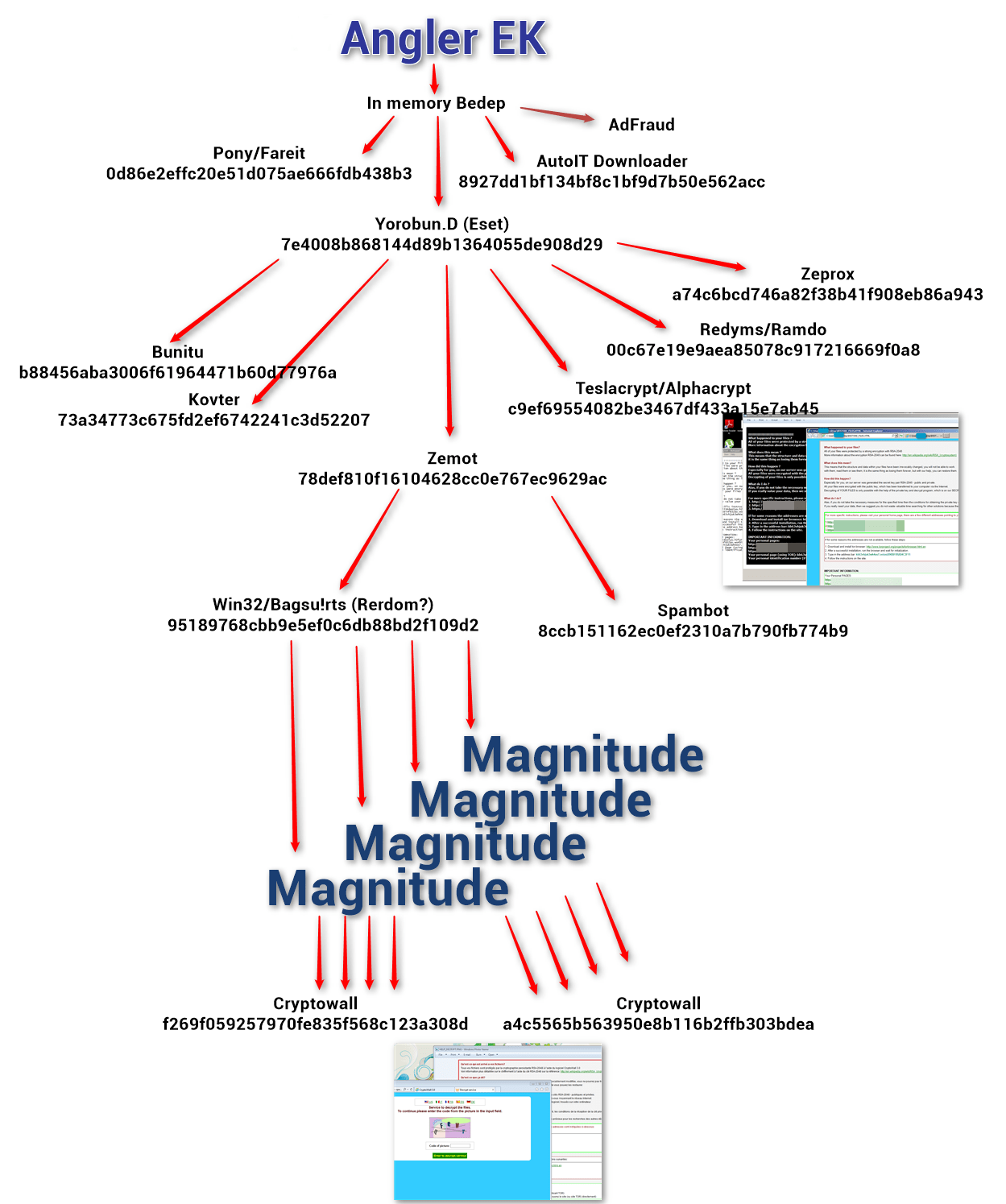
Figure 3: Diagram of observed infection chain from a single malvertising attack
The infection chain reveals a string of affiliate bot owners, starting from the Yorobun [3] owner, compounding infections deliver – in a single pass by the client – nine additional payloads, including pulling in a different EK to deliver two different varieties of ransomware. TeslaCrypt [4] (aka AlphaCrypt) is the first attempted ransomware install (Fig. 4), followed by CryptoWall [5] (Fig. 5).
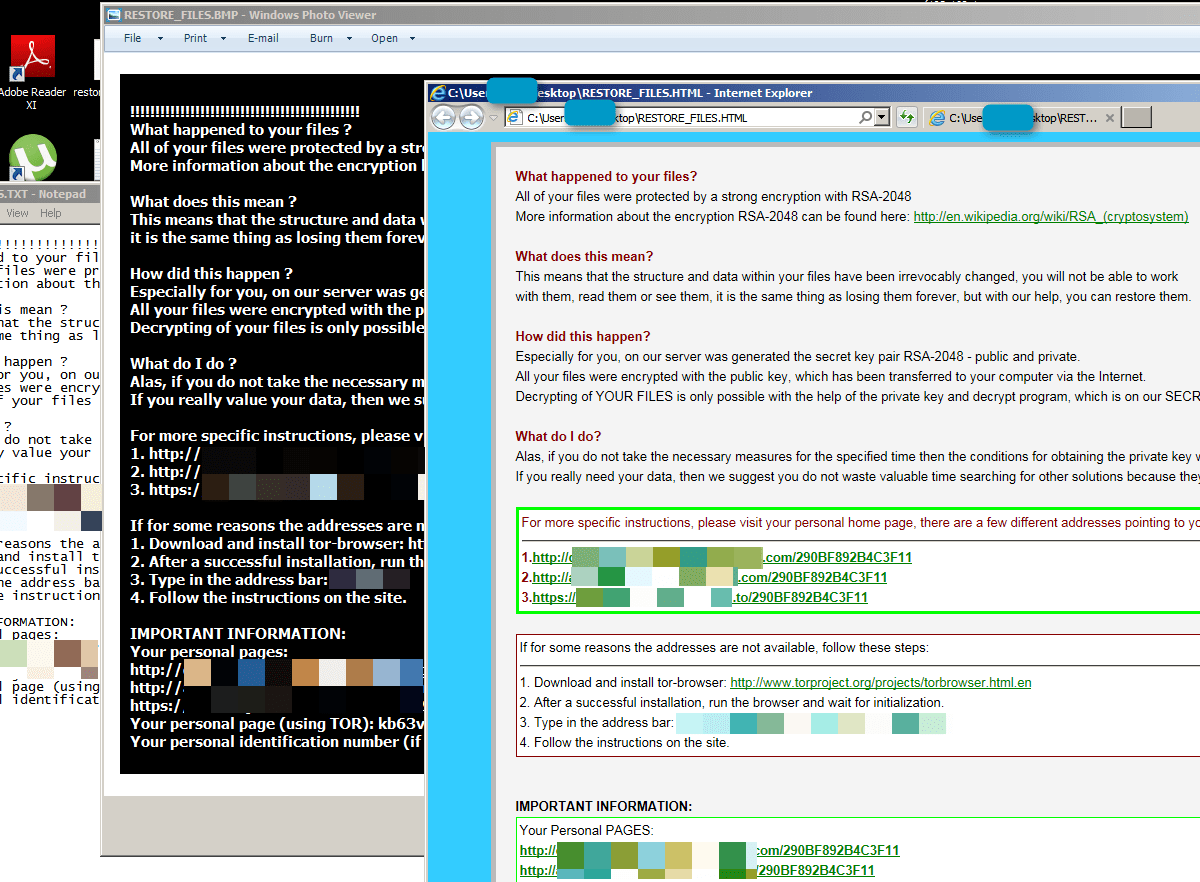
Figure 4: TeslaCrypt (aka AlphaCrypt) ransom message to end-user
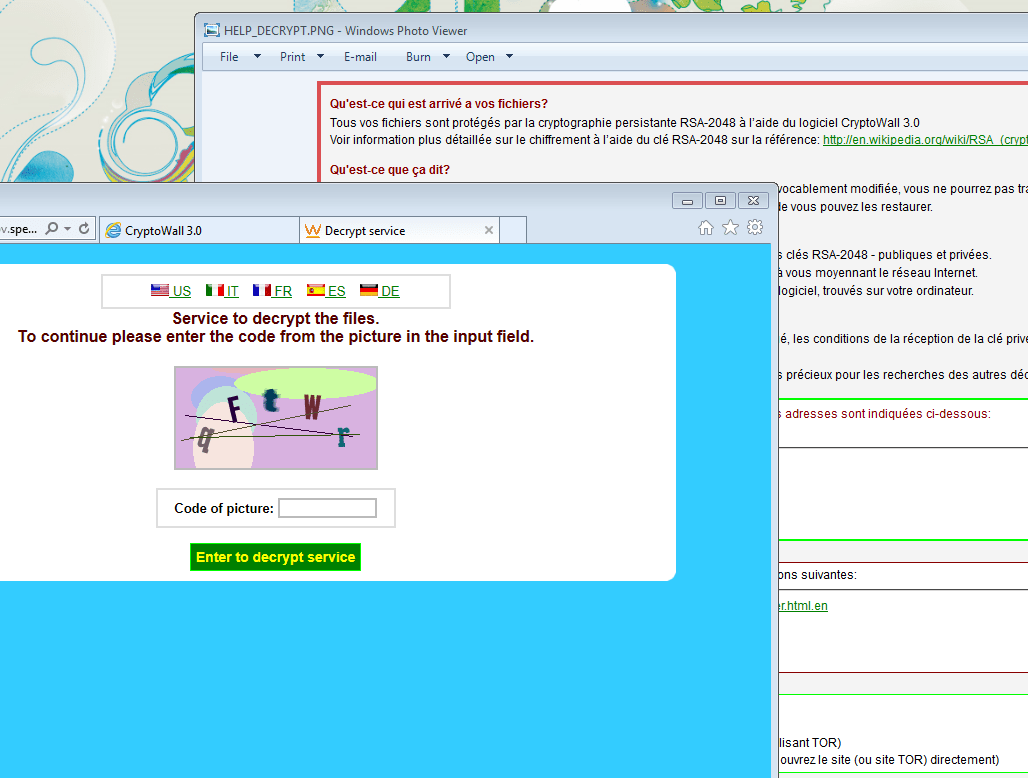
Figure 5: CryptoWall ransom message to end-user
In addition to the double-whammy of two different ransomware infections, this clown-car infection chain also drops Bedep, a click-fraud malware that employs a domain generation algorithm (DGA) for its command and control (C2) communications [6]. The Angler EK drops a payload (first Pony [7], then Yorobun) that is not only followed by five more malware payloads, but also pulls in another exploit kit – Magnitude – which in turn drops at least two variants of the CryptoWall ransomware. Although less well-known than Angler, Proofpoint analysis finds that the Magnitude exploit kit has been one of the three or four most used EK’s over the last 90 days, averaging over twelve percent of total EK traffic.
Rental of an exploit service can cost an actor up to thousands of dollars per month, so it is natural for actors to want to maximize their chances at infection by using malware payloads rendered “Fully Undetectable” (or FUD) by obfuscation services and aggressively selling traffic and spam services. Conversely, high demand for a particular EK can tempt the owner to maximize their revenue opportunity by selling every infection opportunity to as many affiliates as possible. As this example shows, this can lead to payload after payload dropping out of a long infection chain that highlights the fact that today’s infections are rarely matter of a single exploit delivering a single payload… and in this case resulting in a client that is for all intents and purposes unrecoverable.
Despite the entry of new, smaller players, the exploit kit market continues to consolidate around Angler, although it has yet to approach the dominance of Black Hole. While this overloaded infection chain appears to be unusual, it highlights the flexibility and continued threat of exploit kits and the challenge they pose to organizations.
References
[1] https://threatintel.proofpoint.com/
[2] http://blogs.technet.com/b/mmpc/archive/2014/09/09/msrt-september-2014-zemot.aspx
[4] https://blog.kaspersky.com/teslacrypt-20-ransomware/9314/
[5] http://www.darkreading.com/endpoint/clever-cryptowall-spreading-via-new-attacks/d/d-id/1321097
[6] https://asert.arbornetworks.com/bedeps-dga-trading-foreign-exchange-for-malware-domains/
[7] https://isc.sans.edu/forums/diary/Bartalex+malspam+pushing+PonyDyre/19947/
IOCs
- Redirector and referer URLs:
onlinehyips[.]net
hyipmaster[.]name
[hxxp://regular-search[.]com/]
[hxxp://search2015-otoper[.]com/]
[hxxp://homemat-serach2015[.]com/]
[hxxp://domain-searchbest[.]com/]
- File hashes:
0d86e2effc20e51d075ae666fdb438b3 Pony
8927dd1bf134bf8c1bf9d7b50e562acc AutoITDownloader
7e4008b868144d89b1364055de908d29 Yorobun.D (Eset)
b88456aba3006f61964471b60d77976a Bunitu
73a34773c675fd2ef6742241c3d52207 Kovter
c9ef69554082be3467df433a15e7ab45 Teslacrypt / Alphacrypt
00c67e19e9aea85078c917216669f0a8 Redyms
78def810f16104628cc0e767ec9629ac Zemot
95189768cbb9e5ef0c6db88bd2f109d2 Zemot
8ccb151162ec0ef2310a7b790fb774b9 Zemot
f269f059257970fe835f568c123a308d Cryptowall
a4c5565b563950e8b116b2ffb303bdea Cryptowall
a74c6bcd746a82f38b41f908eb86a943 Zeprox
Detection
A complete list of ET Pro and ET Open signatures for the Angler and Magnitude exploit kits is available on the Proofpoint ET Intelligence site at:
Angler EK: https://threatintel.proofpoint.com/text/Angler
Magnitude EK: https://threatintel.proofpoint.com/text/Magnitude
