As part of its risk intelligence and research practices, Proofpoint Nexgate recently analyzed data on social media accounts of ten of the top UK FTSE 100 brands, which include a sampling some of the largest UK firms from Media, Financial, Retail, and Pharmaceutical companies. The period of data spans from Jan 1, 2014 to Feb 3, 2015. The data includes Facebook, Twitter, YouTube and GooglePlus accounts and represents 82 million engaged users, consisting of Likes, Followers, Subscribers, and Plus Ones across 20 authorized accounts. In total, we found there to be at least 3,800 accounts related to the top ten UK brands.
The largest of the UK brands analysed has on average 325 accounts, which is very consistent with findings that the top Fortune 100 US accounts had on average 340 accounts. However, compared to the Fortune Top 100 social media accounts, UK brands exhibit two times as many unauthorized accounts for every verified or authorized account on both Facebook and Twitter. As a result, for the ten UK brands, four of every five (80 percent) of Facebook accounts are unauthorized, and two of every five (40 percent) of Twitter accounts are unauthorized. Unauthorized accounts include fraudulent accounts that impersonate the brand with the intent of ripping off consumers, protest accounts that attack the brand, partners using the brand without approval, and simply third parties trying to leverage the brand to attract an audience to their message. For instance, here is an example of an unauthorized Sainsbury Twitter protest account:
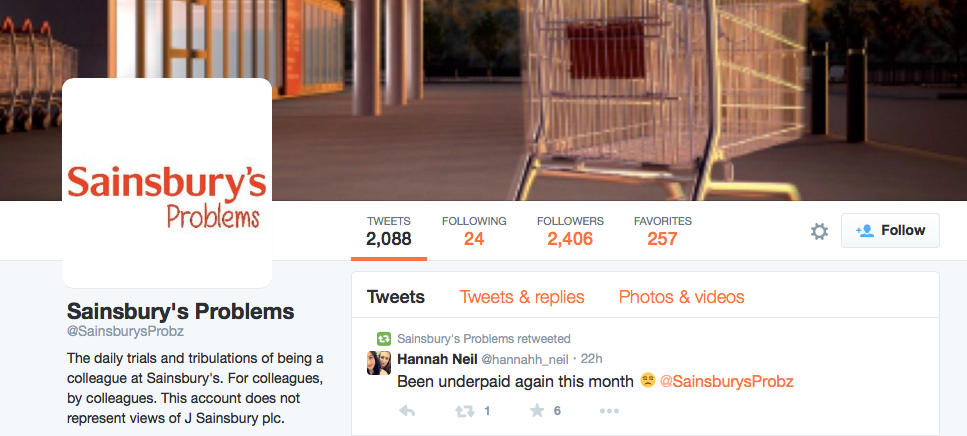
Unauthorized accounts are not always visibly hostile to the brand they are copying. Here is an example of a Rolls-Royce Facebook page that claims to be its official account:
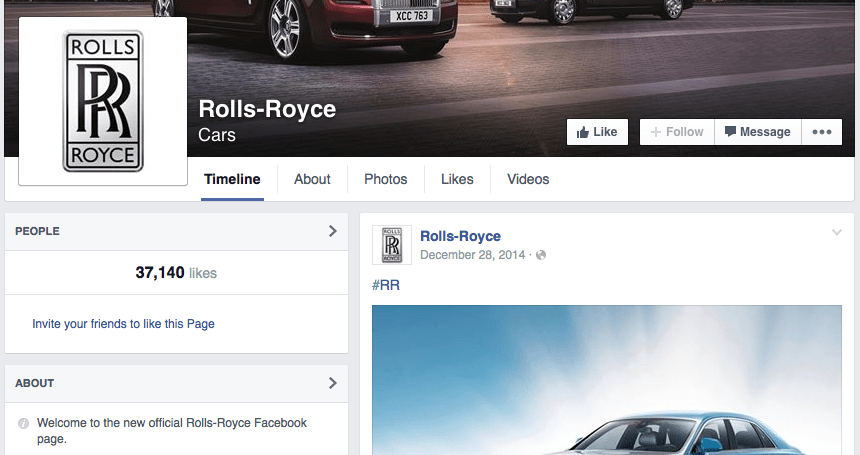
Compare, this with the verified and authorized official Rolls-Royce Facebook page:
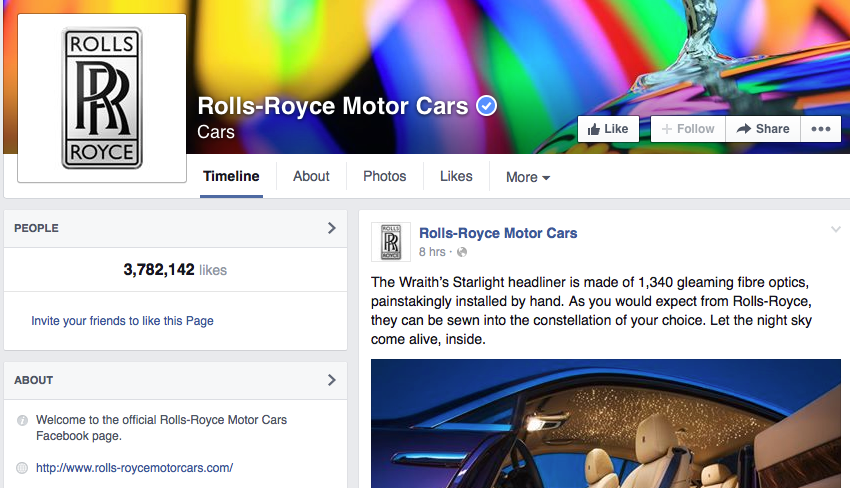
The pages of the two accounts are very similar, and the unauthorized Rolls-Royce Facebook page could easily lure in an unsuspecting audience.
Proofpoint Nexgate researchers found 720,899 pieces of content spread across all 20 authorized accounts on 120 distinct applications, where roughly 62,115 are content generated by the companies themselves, and 658,784 are generated by the brands’ audience. Compared to the Fortune Top 100 social media accounts, the UK social media brands are 20% more active than their US counterparts. On average, there are 45,721 pieces of communication per company. Similar to the Fortune 100 US accounts, Media accounts lead in terms of level of communication activity, and are responsible for 75% of all social media comments.
Of these posts, tweets, and comments, 3,000 consist of spam content. Compared to the Fortune Top 100 US firms, this represents a 60% increase of spam. This increase in spam could mean that there are fewer protective measures in place; data consistent with earlier posts on threats targeting the UK and anecdotal evidence that UK investment in such protective technologies lags that of the US. Approximately 70% of the spam content includes work-from-home schemes that claim the user can make “easy money” working from the comfort of their home, such as the example below in a reply to the ITV News’ post on its authorized Facebook Page:
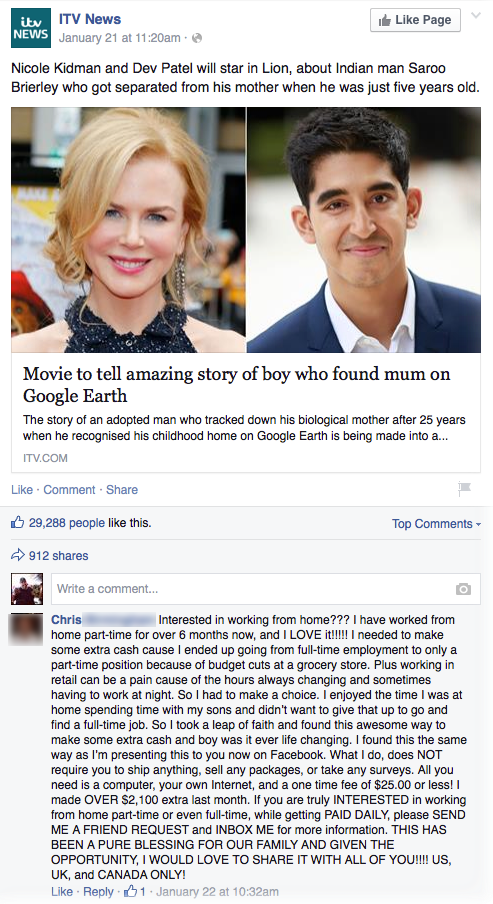
As the engagement numbers on the post shows, this comment from the poster “Chris” potentially reached a minimum of 30,000 engaged users (those who “liked” the post), and this single spam post had the potential to reach hundreds of thousands in the ITV community. Furthermore, Proofpoint Nexgate detected the exact post six times over the span of a week on the same Facebook account, multiplying the number of views of the work-from-home scheme. Messages like these distract the user and pollute the messages that the brand is trying to send, but also highlight the efficiency of social media spam compared to its email-based counterpart: while it might take tens of thousands of unsolicited emails to reach a single user, a single spam social media post can reach tens of thousands of users.
And this is a relatively small-scale example: within the authorized accounts analyzed, the highest engagement activity for a particular account reached up to 14 million followers, which means this many people can potentially see a post from the brand whose comments include scams and malicious content.
Looking beyond spam to more malicious content, we found 161 instances of real security risks, which include content that leads to malware, phishing and other malicious activity. Since the average number of “likes” on a particular post is about 1,000, malware and phishing attacks are reaching 161,000 people.
The following is a typical example of Malware detected on a Facebook Page that uses a very common tactic to lure users:
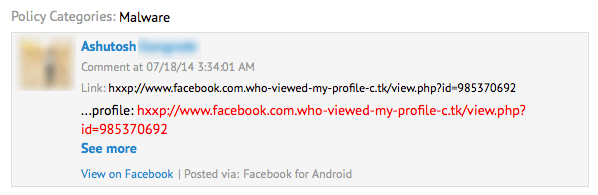
The post claims that the user can see who viewed their profile by clicking the link. (Another popular malicious app promises the ability to change the color of their Facebook app UI.) Clicking on the link takes the user to a page to install the app:
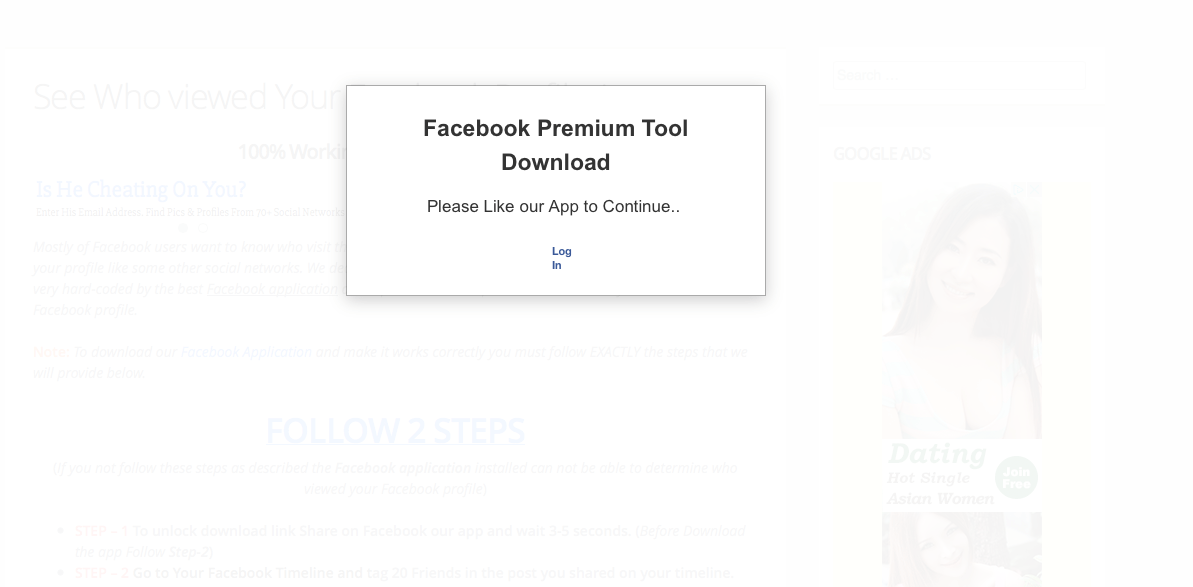
Upon clicking the link, the app asks to share the link by posting an announcement on your wall:
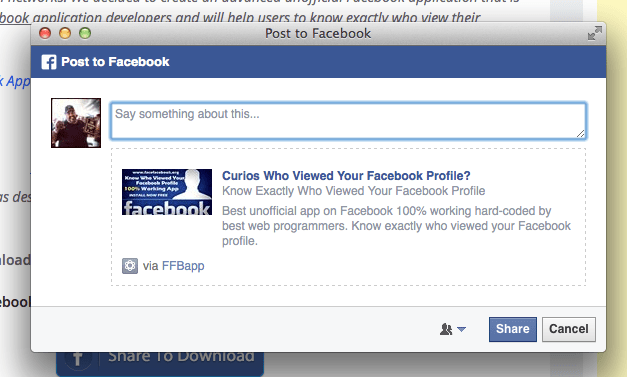
Clicking on the link from this announcement brings the user to a malware download site:
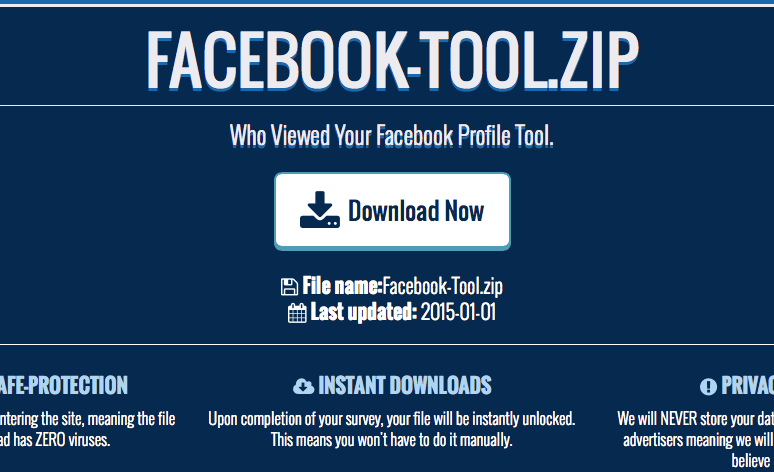
Downloading and running the “Who Viewed Your Facebook Profile Tool” installs malware on the end user’s system.
In an interesting twist on the usual malicious link, Proofpoint Nexgate researchers also identified a Phishing and Fraud link in a post which in fact included a link to a Malware download.
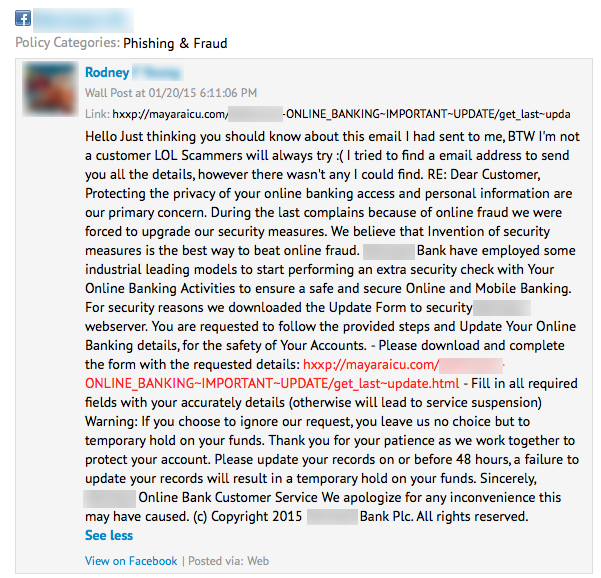
Unlike a standard malicious post, it appears that the end user was in fact attempting to alert site administrators to malicious activity, but in so doing the link the user shared was exposed to hundreds of thousands of users, inevitably at least some of whom will click on this link, as Proofpoint research has found. This represents a case where a simple user blacklist would not have been an effective defense against the propagation of malicious links, since harmful links might not even come from the bad actors themselves as the example above demonstrates.
Phishing and spam content were not the only inappropriate or sensitive content detected in these accounts. Proofpoint Nexgate analysis found 1,500 incidents of regulated data, which includes personally identifiable information such as phone numbers, emails, username and passwords, and even bank account numbers, posted in the social media accounts of the top ten UK brands.
In addition to the posts containing phishing, spam, and inappropriate or sensitive content, the social media accounts of the ten UK brands showed that they suffer from the same process challenges as the Fortune 100 social media accounts. We found that 35% of social publishing done by the UK brands is through a professional tool, consistent with the Fortune 100. Social media best practices dictate a workflow for posting that includes the use of specialized tools (such as Hootsuite or Sprinklr) for posting to corporate accounts. Proofpoint Nexgate research determined that for each of the top ten UK brands, there are on average nine different apps being used to post or tweet content, which means there are nine apps that brands must account and monitor. The equivalent figure for the US-based Fortune 100 brands was fourteen apps, which means the difference between the US and UK social media practices is one of degree, rather than of substance: a profusion of tools undermines the ability of organizations to monitor and control the content of their authorized social media accounts, leading to material that can be at best a distraction, and at worst a liability for the brand and its followers. It also increases the risk of account hacks – the more apps, devices, and people that have access, the larger the potential attack surface for bad actors. There are more doors into the account whose locks can be picked, and is confirmed by the recent numerous social account hacks.
Putting this into perspective, the pervasiveness of social media use by and for UK enterprise brands is significant, and, actually, equivalent to that of the U.S. Fortune 100. At the same time, the risks and threat activity for UK enterprise brands are trending higher. This is likely due to the lack of visibility and focus on social media threats and risk vectors. To protect their investments, their audiences, and to close social media backdoors into the rest of their communication infrastructure, UK enterprises should endeavor to understand their social media infrastructure and take action to deal with the bad actors looking to defraud them, distribute malware on their accounts, perpetrate scams, and attack their brands’ assets.
To do this, enterprises need to find and track their social media account infrastructure, create security policies for those accounts, create security processes around those accounts, and use technology to drive visibility, enforcement, and measure effectiveness of those social media security practices. For a good demonstration of how this approach could be implemented, take a look at the latest Social Threat Center technology from Proofpoint here.
Subscribe to the Proofpoint Blog

